STANDCON CTF - Specimens
Description
Collected a bunch of specimens on our last run, wonder if there is more we misplaced.
http://20.198.209.142:55042The flag is in the flag format: STC{…}
Author: LegPains
Solution
The website didn’t seem much at first, but looking into the HTML code, we see something interesting:
1
2
3
4
5
6
7
8
9
10
11
<ul class="nav">
<li class="nav-item">
<a class="nav-link active" href="?specimen=turtle.php">Specimen 1</a>
</li>
<li class="nav-item">
<a class="nav-link active" href="?specimen=meteorite.php">Specimen 2</a>
</li>
<li class="nav-item">
<a class="nav-link active" href="?specimen=astronaut.php">Specimen 3</a>
</li>
</ul>
We see that each of the links in the navbar are pointed to the same page, but with the location of another .php file specified in the specimen parameter! The next step would probably to test for Local File Inclusion (LFI) vulnerabilites.
We first tried specimen=/etc/passwd and got no result, so we appended multiple ../ to the front to get specimen=../../../../../../../etc/passwd and we still got no results! What’s going on? Could the page be doing some form of filtering against ../?
To summarize what we tried, here is a list of payloads and results that let us deduce that it was doing one pass of replacing all ../ with blanks:
1
2
3
4
turtle.php => shows turtle page
../turtle.php => show turtle page
....//turtle.php => no turtle page
....//....//....//....//....//....//etc/passwd => show contents of /etc/passwd
We also observed that submitting an absolute path in specimen will not work as the specimen value might be prefixed with some directory in the code before including it.
Now that we have a full understanding of the protective measures in place, the next step was figuring out where the flag was. CTFs tend to name their flag files as flag.txt, so we tried a few locations and ....//....//flag.txt worked!
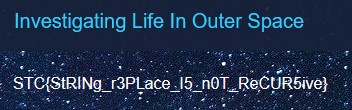
Flag
STC{StRINg_r3PLace_I5_n0T_ReCUR5ive}