TISC 2023 - (Level 1) Disk Archaeology
Description
Unknown to the world, the sinister organization PALINDROME has been crafting a catastrophic malware that threatens to plunge civilization into chaos. Your mission, if you choose to accept it, is to infiltrate their secret digital lair, a disk image exfiltrated by our spies. This disk holds the key to unraveling their diabolical scheme and preventing the unleashing of a suspected destructive virus.
You will be provided with the following file:
md5(challenge.tar.xz = 80ff51568943a39de4975648e688d6a3Notes:
challenge.tar.xzdecompresses intochallenge.img- FLAG FORMAT is
TISC{<some text you have to find>}Attached Files
Solution
After downloading the challenge’s file, I used the file command to determine the method to decompress it.
1
2
$ file challenge.tar.xz
challenge.tar.xz: XZ compressed data, checksum CRC64
A quick search on the Internet reveals that it can be decompressed like so:
1
2
$ tar -xvf challenge.tar.xz
challenge.img
Now that the original file was ready, we can finally start on the challenge.
I used the file command again to determine the file type of challenge.img:
1
2
$ file challenge.img
challenge.img: Linux rev 1.0 ext4 filesystem data, UUID=2b4fee55-fd5f-483c-a85f-856944731f0f (extents) (64bit) (large files) (huge files)
Normally I would throw this kind of file into specialized forensic tools such as FTK Imager or Autopsy, but I decided to test for low-hanging fruits such as seeing if I could retrieve the flag by simply running strings on it.
1
2
$ strings challenge.img
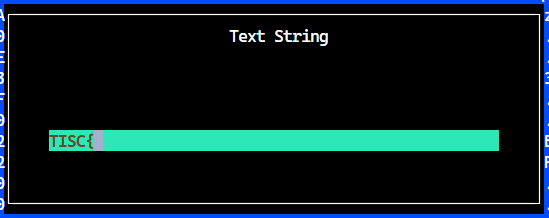
TISC{w4s_th3r3_s0m3th1ng_l3ft_%s}
Oh? It seems that I got a hit and it seems like we almost got the flag! What’s interesting is the presence of the %s, which is the format specifier for a string when you do string formatting in C or Python. Hence, I was able to deduce that we will probably need to run something such as an executable or a script to obtain the full complete flag.
I opened challenge.img in hexeditor so that I could understand what I was working with.
1
$ hexeditor challenge.img
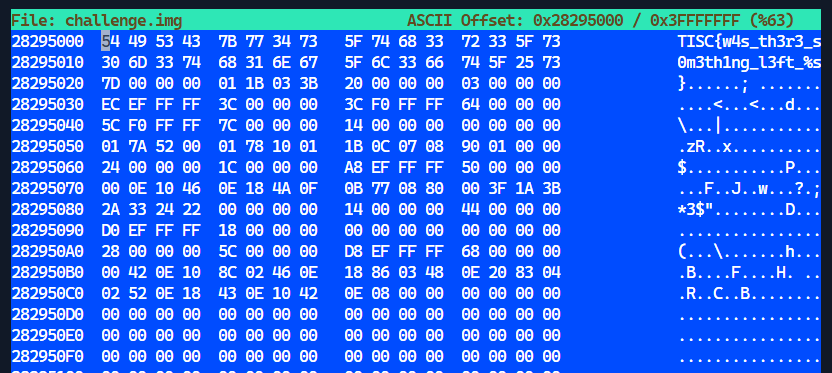
A search for the partial flag was then performed:
The search showed that the partial flag is seen at address 0x28295000 of challenge.img:
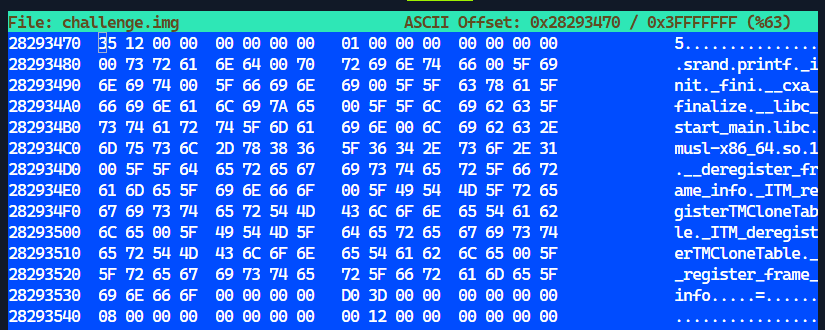
Scrolling up a little, a few interesting strings were observed:
These strings indicated that the partial flag was part of a Linux binary. To extract the Linux binary, the address range of where it resides in challenge.img needs to be determined.
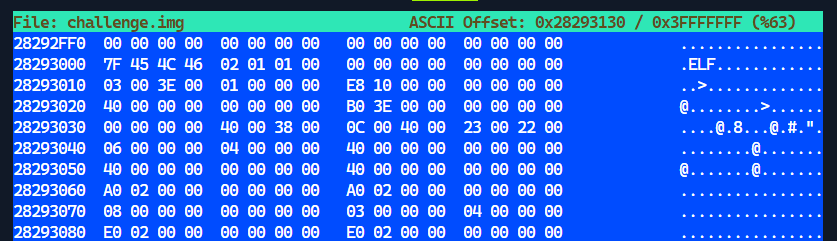
This can be done by scrolling further up until the ELF file signature is spotted:
The starting address is determined to be 0x28293000. While I could have went ahead and determined the ending address, I realized there was actually no need since any extra bytes after the binary will simply be ignored when it is executed.
The following Python script is then used to extract the Linux binary:
extractor.py:
1
2
3
data = open("challenge.img", "rb").read()
exported = data[0x28293000:]
open("mystery.bin", "wb").write(exported)
1
2
3
$ python3 extractor.py
$ file mystery.bin
mystery.bin: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-musl-x86_64.so.1, with debug_info, not stripped
The extracted Linux binary is then executed and the complete flag is displayed:
1
2
3
$ chmod +x mystery.bin
$ ./mystery.bin
TISC{w4s_th3r3_s0m3th1ng_l3ft_ubrekeslydsqdpotohujsgpzqiojwzfq}
Flag
TISC{w4s_th3r3_s0m3th1ng_l3ft_ubrekeslydsqdpotohujsgpzqiojwzfq}